Mobile Phone Forensics And How it Effects YOU
Mobile Phone Forensics
And How it Effects YOU
Kevin Law
(Written for Digital Forensics FOR240)
December 9th, 2012
Abstract
Mobile phones are insecure pieces of technology that people trust all too much. A digital forensic investigator can extract data from these devices to work with or against you. An attacker can also do the same. Text messages, call logs, contacts, media, etc… are all vulnerable to extraction. Mobile phones are also tracking devices. It is entirely possible to track where it has been and a current location in a number of ways. Some of these ways do not even require interaction with the phone itself. It is also good practice to not always trust the source of a caller or the number displayed on the screen. Spoofing phone numbers has become a menial task for anyone with an active internet connection. A forensics investigator would have to get data from the carrier in order to detect a spoofed call. New technology that allows us to pay for things wirelessly in close proximity is being included in mobile phones. This technology can be easily exploited.
Introduction
Cell phones are an item that everyone is carrying on their person now. There are over 5 billion cell phone subscribers currently. These devices allow us to communicate wirelessly to other phones via cell phone towers. A variety of data is stored on a cellular phone, and that information can be extracted from a phone with special technology. Mobile phone forensics is not the same as computer forensics. There are some key differences between the two. Cell phones have multiple operating systems, each with various communication standards. The physical evidence is always on the move, unlike computers which are generally stationary. The data on the phone is not necessarily what is important, until put into context with where it’s been and what it has been connected to.
Many people believe that a cell phone is secure because they carry it with them most of the time. This is a false sense of security. Cell phones are just as susceptible to attackers as computers. Most smart phones use persistent logins for applications, and use very simple passwords to unlock the device. Many financial institutions allow mobile banking through an application or text message. All of the work an attacker would have had to do to break into your accounts using tools and crackers, is already done for them by taking your cell phone. Various accounts would be stolen in one deft move.
Forensic investigators can also get access to contents of cell phones using specialized tools. The information they gather can be used in a court of law as evidence. This can be useful when finding phones at crime scenes.
An investigator may find it necessary to track a cell phone. To track a cellular phone, it can be done through the cell phone towers or GPS signal. Some smartphones even keep logs of where they have been. Smartphones are cellular phones that use data or wifi to request emails or browse the internet.
It must be noted that Cellular phones are covered by the Electronic Communications Privacy Act and Title III. This means that certain questions must be taken into consideration when performing an investigation, such as:
When can you search a cell phone?
When can you search a cell phone?
What actions constitute a search?
When can you seize a cell phone?
How do you interact with the cell phone carrier and/or the cell tower owner?
The scope of an investigation is also very important. It is key to only include items that are within the time and relevancy set by the scope
Brief Overview of how Cell Phones Operate
There is quite a bit of variation in phones that are currently offered for sale, however at the root of all of it, any mobile phone is just a compact mobile device run by a battery pack. Nearly every device contains some type of organizer for contacts and appointments. Smartphones have a much larger application base and much more powerful hardware.
Mobile phones are essentially radios. Every mobile device communicates with each other using radio frequencies transmitted by base stations with towers on them. One frequency is used to transmit, while the other is used for receiving. Using two frequencies allow the phone to transmit and receive at the same time. This is called duplexing. Each station is given a certain set of frequencies to use, and they are reusable as long as they are not adjacent to each other. The stations are usually aligned in a hexagonal grid pattern (See Appendix A). This is used for maximum coverage. A tower in a city covers a half mile, and around five miles for a rural area.
When a person is moving and leaves the signal of one tower, another tower picks up the signal and continues the communications. This is called handing off the signal. It has become so sophisticated that it can be done without the end users knowing. According to an analysis by Saxena (2009), the process is such that the tower that a user is connected to notices that the signal is degrading, while another tower nearby sees the signal improving from the user. When the signal from the second tower overpowers the first tower, the device switches to the second. A hard handoff occurs when the second tower uses a different frequency then the first tower. When a hard handoff is necessary, it causes a service interruption. A soft handoff is when the towers use the same frequency, this allows for a device to be connected to multiple towers at once using the same frequency, choosing the best signal to communicate through (p. 2).
Phones use a pathway called a control channel to communicate between the tower and the phone. The phone sends out its International Mobile Equipment Identity (IMEI) gets System identification Code (SID) from the tower and a registration request. The SID is unique to the carrier and can only be changed by requesting an unlock code from the carrier. Providing the SID matches the one programmed in the phone, then the phone will be able to communicate properly. The registration request allows for the tower to track where you are to allow messages and calls to be forwarded to the device properly. Data is sent from the caller through the towers to the receiver letting it know a call is coming through. The tower then pairs the frequencies to communicate through.
Short Messaging Service (SMS) uses the same control channel to communicate. Messages are sent to a Short Messaging Service Center (SMSC). This center stores messages before forwarding them to the recipient. Messages include a header, much like an email does, that contains information such as: timestamp, sender, recipient, length, service center, and protocol (Pettersson, 2005, p. 1).
How is Data Obtainable?
A common problem that forensic investigators run into when given a mobile phone is that there is no universal connection to pull data from. This leads to having a toolkit with a large collection of different tips to be able to interact with the device. Sometimes data cannot even be pulled from these ports, and the only way to do is to actually use the device. This could be a potential problem with data integrity. Stations are made the lock the phone into a stand with a camera directly facing the screen. This allows for taking video or pictures of the investigation process regarding the contents of the phone.
Every phone has a SIM card which contains a unique serial number and the subscriber’s IMSI number. It also can contain the user’s phonebook and saved text messages. It is valuable to analyze the SIM card and pull basic information from it. Jansen and Ayers (2007) recommends using SIMCon to extract data from the SIM, which then puts it into a case file for analyzing. If the SIM is locked with a PUK, then it will be extremely hard to pull the data from it (p. 18).
Smartphones generally use a Micro-USB or Apple’s Dock Connector. This is because a main feature is to provide a simple interface between a computer and the device to transfer music, movies, and pictures back and forth. This makes a forensics investigator’s job much easier because it shortens the amount of adapters needed to carry around and organize. Smartphones usually have a program to manage the phone on a computer, such as Itunes or blackberry. These programs make backups of the phone which can be used to restore data in case of accidental deletion. It is possible to use those backups to analyze a smartphone without ever need the actual device itself.
Cellebrite offers a toolkit that offers logical, physical, file system, and password extraction from a given mobile device (See Appendix B).
According to their website, it can bypass screen locks and password-protected devices. The toolkit can even read a sim card without a phone needed (Cellbrite, 2012).
Encase suite for the computer can image Android, IOs, and Blackberry devices using the usb port on a computer. It then processes the data and makes it available for analyzing.
Steps to properly extract data from a cellular phone:
1.
Obtain as much information about the phone as possible.
There are websites with this information or find the manual online
2.
Find the proper plug to connect to the device
3.
Isolate the phone from all communications
It is extremely important to completely isolate the device from outside communications in order to retain its integrity. Remote wipes on cell phones, overwriting the most recent communication data that the provider has on the device, and skewing the location data are all entirely possible. Programs such as LockMe can be used to locka phone remotely from a text message.
4.
Use software that works with that model cell phone.
Making an image of the phone may not be necessary, so make sure to be able to prove the integrity of the data.
For my Android based phone, I was able to plug it into a lab computer using the Micro-USB interface and image the device in less than a minute. From there the data was processed and ready to be developed into a case file.
What Data is Obtainable?
The data that can be extracted from a cellular device varies depending on the model and the programs used to extract the data. Generally the data that can be extracted can also be viewed on the device, such as: IMEI, network information, contacts, call logs, SMS inbound and outbound, multimedia messages, pictures, and video. More information can be pulled including: server identification, call type for billing purposes, location area code, tower location name, voicemail number, and SMSC number. Smartphones allow a much broader range of data to be extracted. Emails, documents, and GPS locations can be pulled from the phone.
Contacting the provider of the service will grant you access to information provided it is still on record. Some carriers only keep some information for 30 days. Information that can be retrieved through the carrier includes but is not limited to: timestamps and length of calls, incoming phone number, tower number, location, which antenna, and which tower received and ended the call. AT&T charges a fee along with a 2-week waiting period in order to request detailed records. General call logs are available for instant view in their account management panel.
The amount of data that can be extracted is good for forensic investigators because it allows for a more thorough investigation. Getting as much data a possible is necessary to uncover hidden clues. In a case where a person is accused for texting and driving, the person may claim that they were not even on their phone. After gathering the required warrants and obtaining the phone, it is only a matter of time before their claim is put to the test. Extracting all of the text messages and call logs, and comparing it to a timeline of events, that is enough information to hold up in court. If the person was using a smartphone, GPS data can be extracted and could even pinpoint where on the road they were when texts were sent.
In a case with a drug dealer, finding the phone allowed for law enforcement to gather his contacts. Despite it being a prepaid cellular phone with no trace to who it was, through clever investigation they figured it out. After interviewing the numbers extracted from the contacts list, the police determined who it was through process of elimination and successfully prosecuted the dealer.
On the other side of the spectrum, being a victim to having your phone stolen can be a major invasion of your privacy and personal information. If the thief is trained in cellular forensics, it will only be a short amount of time before he has all of the information he needs about you. This could be beneficial for social engineering attacks, or they need your phone for two-factor authentication.
Tracking cell phones
Cell phones are always in communication with the cell tower when in range. This means that the tower knows the general location of the device connecting to it. When an incoming call or text messages is directed at the device, the exact location is known by the tower. This information can stay can at the tower and be used to plot out where the device has been. A user can be tracked in real time this way regardless of being on a call or not.
Government officials have started using a new way to get a precise up to date location of a mobile phone. They developed what they are called a “Silent SMS”. A silent SMS is essentially an empty text message with parameters set so it does not alert the user they have received it. It is basically just a ping that the device cannot detect. That ping updates the location back to the tower for officials to track.
This type of tracking is easily done by writing a text messaging program and entering the parameters listed in Appendix C. It can be used for harm though if used maliciously. “However, the very technology that has helped tracking criminals also has the potential to become a channel for launching cyber attack. It has the potential to be a channel for launching DoS attack, triggering malware etc. Henceforth adequate security assurance must be implemented for mobile devices” (Arnabc, 2012, p. 1).
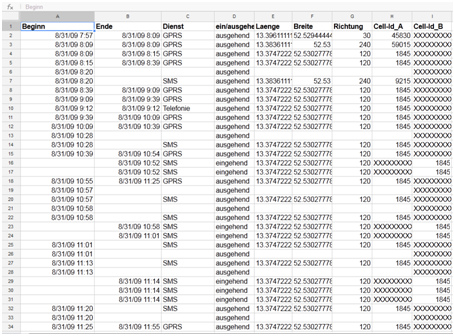
A man in Germany requested the data that his provider had from his phone. He ended up having to sue the company to get that data, but in the end they handed over a very large excel spreadsheet (See Appendix D). At first it looks intimidating, but the man wrote a program to map it out on Google Maps which then made points in time to be played back. The end result was a very accurate path he chose and when he used his phone for what use. It also showed where each cell tower was and his signal strength, with handoffs to other towers as well. When he lost signal, the program predicted its path to the next point(Spitz, 2009).
Another form of tracking requires a GPS enabled phone. Most smartphones contain a GPS in them for use of getting directions. A lot of users leave the GPS on and forget to turn it off. Some malicious apps have been written to send live GPS data back to an attacker. When a forensic investigator dumps the contents of a smartphone, depending on the type of phone, it will also dump all of the GPS data. GPS data is extremely accurate up to a meter.
Peter Warden found a file on his iPhone 4 labeled “consolidated.db”. It turned out to be a database of everywhere he has been with his iPhone. He wrote a program to map it onto Google Maps to see how accurate it was. The data was being pulled from cell tower signals, and not precise GPS data. iPhones are storing cell tower information on the device itself, instead being at the tower base station. To make matters worse, it was in an easily accessible file unencrypted. All of this is done without the owner’s permission. “By passively logging your location without your permission, Apple has made it possible for anyone from a jealous spouse to a private investigator to get a detailed picture of your movements” (Warden, 2011)
A forensic investigator may want this information to see where a person has gone, say, for drug deals or robberies. It can also be used to predict where someone is going next. All of the data pulled can accurately tell a person’s patterns. An attacker could use this information to see when a victim is going to be out of the house.
Spoofing
To spoof a phone number, is to pretend you are that phone number. So for example, you call your son and he refuses to answer you. You then spoof one of his friend’s phone numbers and he picks up on the first ring, because to him it looks like his friend is calling. Spoofing a phone number can be done very easily with modern technology. There are websites that can do all the hardwork for you and have you spoofing phone numbers within a minute. Due to the Caller ID Act of 2009, it is now illegal to spoof numbers to cause harm or fraud. This does not stop people from doing it though.
It is possible to spoof a phone number to listen to the voicemail of that device. Caller ID is always trusted. Kevin Mitnick is famous for his social engineering attacks, which involve spoofing phone numbers to pretend to be people of high authority. The only way to determine a spoofed phone call is by checking the provider’s records to see if the numbers line up. Once the origin of the call is tracked back to the spoofing service, then further action can be taken on that service.
Spoofing the sender of a text message is a bit harder, but still possible. It is done by writing the raw format encoding that SMs uses called Protocol Description Unit (PDU). The PDU has all of the header information of the text, much like an email would. By making a custom PDU, it is possible to change the sender number and the reply address. This is easier said than done, as it requires buying software or coding it yourself to be able to send raw PDU’s.
To see what the raw data of a text message spoof looks like, an example is provided:
Hexidecimal PDU Message:
07911326040000F0040B911346610089F60000208062917314080CC8F71D14969741F977FD07
Output in 7 bit:
|
SMSC#+31624000000
Sender:+31641600986
TimeStamp:26/08/02 19:37:41
TP_PID:00
TP_DCS:00
|
TP_DCS-popis:Uncompressed Text
class:0
Alphabet:Default
How are you?
Length:12
|
Seeing the original PDU data is not possible on every device or the tools used. Using Encase v7 on an android phone, it was not possible to view the PDU data on a text message.
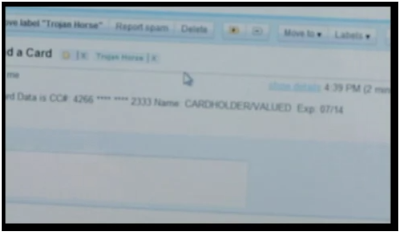
A man in Phillipsberg, New Jersey was arrested for violating a restraining order by sending a flurry of text messages, most of which were in the vulgar nature. After investigating the text messages sent and extracting data from both of the phones, the texts that were sent were spoofed to be in his name.
Another uncommon form of spoofing is spoofing a cell tower. This is a very dangerous attack that can be done for about $1,500 in hardware according to Chris Paget at Defcon 17 conference (Zetter 2010). It consists of setting up your own antenna to a computer running software that will mimic a GSM network cell tower. Because of how handovers work with cell towers, if the antenna is close enough your phone will connect to the spoofed tower. Then the attacker can see everything your phone is trying to communicate. This is essentially a man in the middle attack for cell phones. “’As far as your cell phones are concerned, I am now indistinguishable from AT&T,’ he said. ‘Every AT&T cell phone in the room will gradually start handing over to my network’” (Zetter, 2010).
Dirty Cell Phone Hacks
Spoofing is an uncomforting concept for a cell phone user. That is only one of the many hacks that can be directed at a cell phone.
One in particular involves the use of emerging technology called Near-Field Communications (NFC). This allows for establishing a connection by proximity. New smartphones come with this technology enabled. Some of the legitimate reasons for having NFC on a smartphone include:
Google Wallet – Storing cards in your phone to easily pay for items by transferring through NFC
NFC tags – Change your phones settings when you get home, enter your car, or go to a coffee shop. The tags can set preset settings, like enable Wifi, disable GPS, Turn phone on silent, etc…
The vulnerability is in these payment systems that allow you to pay easily with NFC. The technology is the same in RFID enabled credit/debit cards to allow for contactless payments. Apps have been written that can read nearby cards and steal the information from them. This used to be done with a device the size of a briefcase, now it can be done with your phone. Imagine walking around a convenience store and leaving with everyone’s credit cards on your phone. An attacker could even take your card, then pay for an item right in front of you with it.
Taking it a step further, at the Shmoocon hacker conference in Washington DC, Kristin Paget wirelessly stole a volunteer’s credit card. Then she used a card magnetizing device with a blank card and wrote the data onto a card. “A second later, she used a $300 card-magnetizing tool to encode that data onto a blank card. And then, with a Square attachment for the iPhone that allows anyone to swipe a card and receive payments, she paid herself $15 of the volunteer’s money with the counterfeit card she’d just created” (Greenberg, 2012). This makes the scam look that more legitimate.
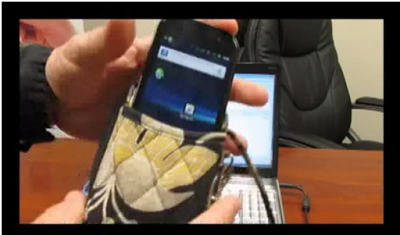
Taking it even one more step further, YOU probably have a smartphone and a credit/debit card with a contactless payment system. Well, you could download an application that is backdoored with a program to turn on your NFC and take the cards wirelessly right out of your wallet! And then it will send the numbers back to the attacker, all without you knowing! This is a perfect attack because people usually put their phones so close to their wallets, or they eventually end up in close proximity. Walt Augustinowicz of Identity Stronghold demonstrates just how easy this can be done with his demonstration video online (See Appendix E).
Stealing credit cards through an NFC enabled phone takes identity theft to a whole new level. Trying to prove how your card got stolen may be very difficult, but if the backdoored application is found on your phone through an examination, the attacker may be able to be found. A forensic investigator may obtain a phone with the application and stolen credit cards hidden away. The chances are slim, but if this style of attack becomes more known, then it may be easier for the good guys to catch the bad guys.
Security measures have been taken to prevent this from happening. Some cards use a one-time CSV code, which means the attacker has to use the card before they do. If an attacker does use it, it can only be used to make one purchase, instead of many small ones.
References
Saxena, Shalini (2009). Statistical Approach for Analyzing Cell phone Handoff Behavior. Retrieved from http://www.scientificjournals.org/journals2009/articles/1444.pdf
Pettersson, Lars (2005). SMS and the PDU Format. Retrieved from http://www.dreamfabric.com/sms/
Jansen, Wayne & Ayers, Rick (2007). NIST Guidelines on Cell phone ForensicsRetrieved from staff.sjci.com/cis/Forensics/Notes/Cell%20Phone%20Forensics.pdf
Cellebrite (2012). UFED Ultimate: Logical and Physical Extraction of Mobile Data. Retrieved from http://www.cellebrite.com/mobile-forensic-products/ufed-ultimate.html
Arnabc (2012). Silent SMS: How I Know Where You Were Yesterday Night. Retrieved from http://www.ivizsecurity.com/blog/security-awareness/silent-sms-how-i-know-where-you-were-yesterday-night/
Spitz, Malte (2009). Tell-all Telephone. Retrieved from
http://www.zeit.de/datenschutz/malte-spitz-data-retention
Warden, Pete (2011). iPhone Tracker. Retrieved from http://petewarden.github.com/iPhoneTracker/
Zetter, Kim (2010). Hacker Spoofs Cell Phone Tower to Intercept Calls. Retrieved from
http://www.wired.com/threatlevel/2010/07/intercepting-cell-phone-calls/
Greenberg, Andy (2012). Hacker’s Demo Shows How Easily Credit Cards Can Be Read Through Clothes and Wallets. Retrieved from http://www.forbes.com/sites/andygreenberg/2012/01/30/hackers-demo-shows-how-easily-credit-cards-can-be-read-through-clothes-and-wallets/
Appendix A
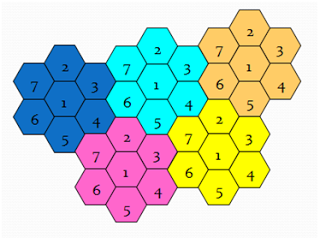
This is the layout that Cellular Towers use. Each number represents a different set of frequencies. Notice how a frequency is never touching itself.
Appendix B
Cellebrite UFED Ruggedized Briefcase
Used in mobile phone forensic investigations to extract data from a device.
Appendix C
Excerpt from ivizsecurity.com Written by Arnabc on August 9th, 2012
http://www.ivizsecurity.com/blog/security-awareness/silent-sms-how-i-know-where-you-were-yesterday-night/
How to create Silent SMS
To create Silent SMS, the SMS PDU (Protocol Data Unit) needs to be manipulated. It is best done from an application that communicates with SMSC (SMS Center) using a protocol called SMPP. To send a SMS, the application need to send SMPP GSM 03.38 encoded Submit_Sm PDU. A sample Submit_SmPDU is shown below:
|
Encoding PDU Header . .’ command length ’ , ( 7 1 ) . . . 00 00 00 47
’ command id ’ , ( 4 ) . . . 00 00 00 04
’ command s t a tus ’ , ( 0 ) . . . 00 00 00 00
’ sequence number ’ , ( 1 ) . . . 00 00 00 01
Encoding PDU Body . .
’ service type ’ , ( 0 ) . . . 30 00
’ source_add r_ t o n ’ , ( 1 ) . . . 01 __ ’ source_ addr_ npi ’ , ( 1 ) . . . 01 **
‘source_ addr ’ , (27829239812) . . . 32 37 38 32 39 32 33 39 38 31 32 00
’dest_addr_ton ’ , ( 1 ) . . . 01 **
’dest_addr_npi ’ , ( 1 ) . . . 01 **
’dest_ addr’ , (27829239812) . . . 32 37 38 32 39 32 33 39 38 31 32 00
’esm_ class ’ , ( 0 ) . . . 00
’protocol_ id ’ , ( 0 ) . . . 00
’priority_flag ’ , ( 0 ) . . . 00
’schedule_delivery_time ’ , ( 0 ) . . . 30 00
’validity_period ’ , ( 0 ) . . . 30 00
’registered_delivery ’ , ( 1 ) . . . 01
’replace_ if_ present_fl ag ’ , ( 0 ) . . . 00
’data_coding ’ , ( 0 ) . . . 00
’sm_default_msg_ id ’ , ( 0 ) . . . 00
’sm_length ’ , ( 0 ) . . . 00
’short_message ’ , ( ivizsecurity.com ) . . . 69 76 69 7A 73 65 63 75 72 69 74 79 2E 63 6F 6D
Full PDU ( 70 o c t e t s + + ) . . 00 00 00 47 00 00 00 04 00 00 00 00 00 00
00 01 30 00 01 01 32 37 38 32 39 32 33 39 38 31 32 00 01 01 32 37 38
32 39 32 33 39 38 31 32 00 00 00 00 30 00 30 00 01 00 00 00 00 73 61
74 6E 61 63 2E 6F 72 67 2E 7A
** ( 0 ) indicates local numeric numbering formatting
( 1 ) indicates international numeric number formatting
++ Octet is a group of 8 bits , often referred to as a byte
|
Appendix D
Appendix E
Walt Augustinowicz of Identity Stronghold shows us how his backdoored program is used to steal credit cards using NFC.
https://www.youtube.com/watch?feature=player_embedded&v=eEcz0XszEic#!