Analyzing Malware with Cuckoo
From their About page:
I am using Xubuntu 13.10 as the host machine for the lab. It is running inside of a Virtual machine for portability. Cuckoo is running version 0.6.In three words, Cuckoo Sandbox is a malware analysis system.What does that mean? It simply means that you can throw any suspicious file at it and in a matter of seconds Cuckoo will provide you back some detailed results outlining what such file did when executed inside an isolated environment.
Inside of the Xubuntu install, I have a Windows XP SP3 and a Windows 7 virtual machine on a VirtualBox install. Both of these machines have usual user applications, like Firefox, Adobe Reader, Java, etc...
In order to use a virtual machine with Cuckoo, snapshots of the machine must be made for Cuckoo to start and revert back to. Upon uploading a sample, Cuckoo will restore the machine, execute and analyze the sample, and then revert the machine back to the snapshot.
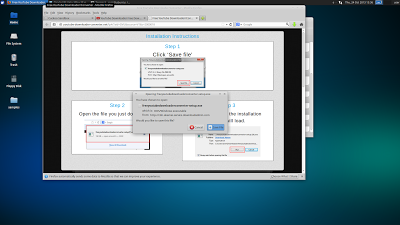
Here is an overview of the steps to use Cuckoo
|
|
|
|
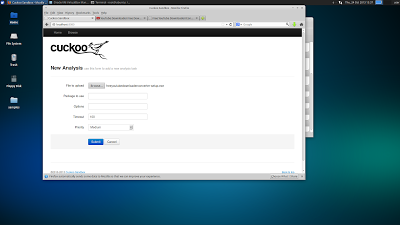
| The WebUI works very well. |
I went searching for Youtube Downloaders for malware samples. Aimbots and Cracks are good keywords to look for as well.
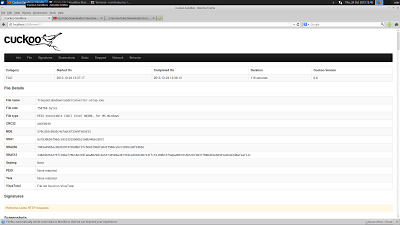
There is a WebUI for uploading samples that works very well. There are many different package types that can be analyzed, like .jar, .pdf, and .zip's. Cuckoo does an excellent job and executing samples.
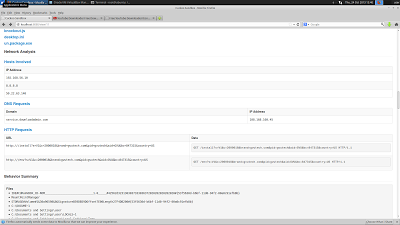
After analysis is complete (usually 10-120 seconds), you get a nice printout of what cuckoo found. It also stores all this information on the host, so you can download all the pcap's and logs to have analyzed with another tool, like Wireshark.
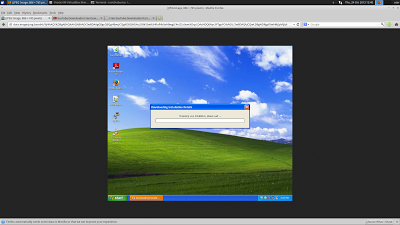
Cuckoo takes screenshots everytime something changes on the screen. It will do it's best to automate installers too.
Because Cuckoo analyzes the traffic, it prints out what IP's and DNS addresses it attempts to connect to. This is invaluable information when trying to reverse and track malware.
|
|
|
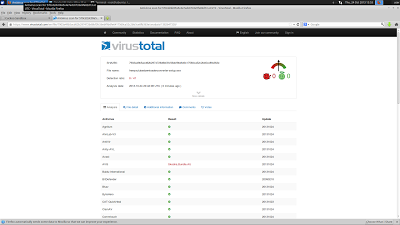
This particular sample was not in the Virus Total database, so I uploaded it to have it analyzed by virus scanners for malicious intent. This sample was DownloadAdmin, an adware/PUA dropper.
It is common for malware to reach out to it's command and control domain once installed. They may also connect out and download more payloads. Cuckoo can capture those connections.
|
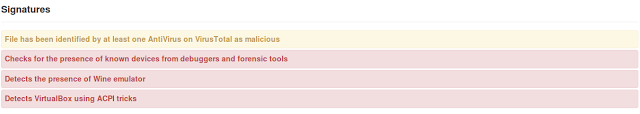
| Cuckoo will tell you if the malware is aware of virtualization. |
Cuckoo Sandbox makes automating malware analysis trivial. In my opinion, Cuckoo is a great starting point for analyzing a sample. It gives a wide range of useful information and displays it in an easy to read format. Some malware can detect if it has been run inside of a virtual machine, which is where Cuckoo falls short. Since Cuckoo is dependant on virtualization, you will only get a readout of hashes and a warning if the malware has a virtualization detection feature. Using a physical machine would be necessary for further analysis at that point.