Raspberry Pi Dropbox Pentesting Tool
I finally got my hands on a Raspberry Pi to play around with. I could see the potential for malicious intent as soon as I saw it. The first thing I did was order a low profile microsd card adapter. This takes care of the obnoxious sd card sticking out the back, and allows for easier hiding of the Pi.

|
| Check out the slick low profile microsd card adapter |
I wanted the Pi to do a few things for me:
Only require Network and Power
Call back to control once it was powered on
Recon the network and report back
Allow me to remote in and manually exploit
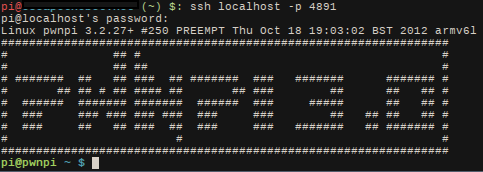
I looked at the various pentest distros for the Pi. I ended up with PwnPi. After seeing the little power this thing has, I would've been more comfortable with Raspbian. I say this because PwnPi takes forever to do things. Metasploit takes about 15 minutes to start up. I'm using a class 10 SDHC card as well. It's just nice to know the tools are available if I desperately needed them.
After loading up PwnPi, I made a user called "pi". I generated ssh keys so it can ssh into my control server without a password. I made a user on my control server called "pi" as well. (And added the usual key-only login security measures, etc...)
Now that we have ssh keys and a server to callback to, we can setup a script to automatically callback when turned on:
Loading ....
Save as foo.sh , and drop it in a folder on the pi. Then make a crontab for this to run every minute or so. That way if connection is dropped, it will keep retrying to connect back.
Now we have most of the requirements that I wanted with that simple bash script. But what if we wanted a little more insight into the network we are connecting into. Opsec is important, and you do not want to be too noisy on the network at once.
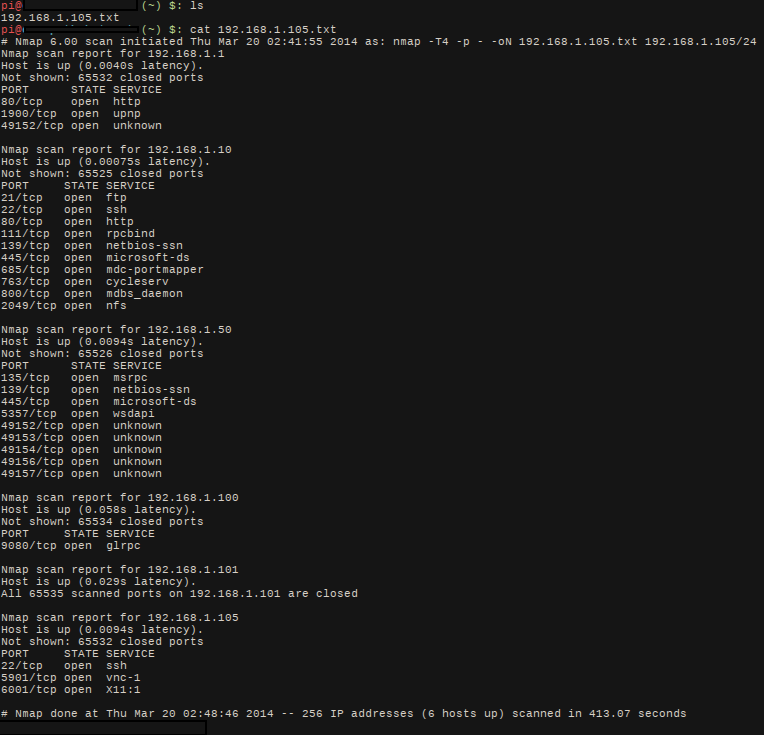
With that in mind, I wrote a dirty nmap script that scans the network and scp's the report back to control:
Loading ....
The output looks like this:
Now you know what exploits you want to run before you even manually connect in and go to work!
Back to what I was saying about the Pi not being all that powerful. It would be ideal to connect in and run exploits right from the Pi. This was not the case, since tools and scans took forever to run.
I ended up ssh tunneling my tools through the pi. Maybe in the future I'll put openvpn certs on it and route all traffic between the network it's on the the vpn. That way I can connect to the vpn and run train from it.
The Rasbperry Pi can be a great tool to have when pentesting or causing havoc (same thing right? :P )
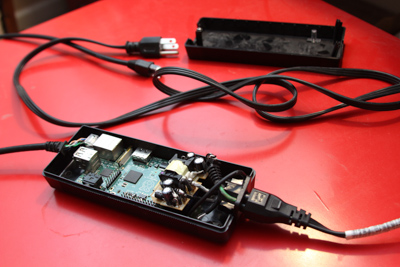
You can put it in a inconspicuous case and no one will give it a second look:
|
| laptop battery case |

|
| Wireless router case |